
Microsoft 365 & Azure Migration Melbourne | Microsoft Gold Partner
Melbourne’s leading Microsoft 365 & Azure migration specialists. Microsoft Gold Partner 22+ years experience. Secure, no-downtime cloud migrations for business.

Melbourne’s leading Microsoft 365 & Azure migration specialists. Microsoft Gold Partner 22+ years experience. Secure, no-downtime cloud migrations for business.

SSL VPN is being retired by the vendors who built it. Here’s what the shift to IPsec IKEv2 and ZTNA means for your remote access strategy
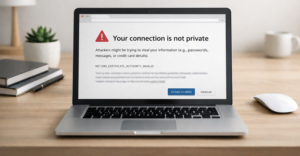
Prepare for the automated 47-day SSL certificate lifecycle. Use our interactive infrastructure audit to prevent silent outages & master the 2026 security shift

An open-source AI assistant’s rapid rise and faster fall offers lessons for every organisation evaluating emerging technology

When you talk firewalls, there are two types that are most commonly used: Traditional Firewall and Next-Generation Firewall (NGFW). What are the differences?
How Intellect IT’s managed services cybersecurity protected Melbourne clients from FortiOS vulnerability FG-IR-24-535. Proactive threat detection and prevention.

Intellect IT recently hosted the first webinar in our “Be Secure”, series titled “Staying Ahead of the Cyber Security Game”. Where we focus on current cybersecurity trends.

The most commonly known and biggest advantage of a next-gen firewall is the advanced security options that are brought to the table.

Protect Your IT Assets With These 8 Policies to ensure your company’s IT resources are used appropriately and productively.

Disasters don’t always come in the form of a pandemic; they can be a cyber attack that results in a data breach, hardware faults, extensive power outages, system failures or operation downtime.